by Dom Bowker
(Updated 11/10/19)
We are probably all too familiar with the regular restarts and updates that our laptops and PCs request to patch the Windows Operating System. Whilst there is probably not anyone that actually looks forward to this task, there is no doubt that Microsoft has certainly improved the process in recent years. The process may have its issues, but for a techie, patching Microsoft servers requires just a few button clicks.
Because of its ability to support various platforms and configurations the picture is more complicated when patching EnterpriseOne (E1) and the underlying technology that supports it. This is probably due, in large part, to the complexity of the process and the specialist skills needed, and partly due to the evolving nature of JD Edwards.
Some E1 customer sites may not be aware that Oracle release security advisories for E1 and there are important security patches available for Oracle products. On my travels as a CNC consultant, it is not unusual to find a customer site where no procedures or policies have been implemented for patching E1, or the underlying technology that supports it (e.g. databases, web servers and other third-party software) that’s required. But with the increasing tendency to connect E1 to the Internet, and the recent news about the ‘Meltdown’ and ‘Spectre’ bugs, it is perhaps timely to review the current patching available for JD Edwards EnterpriseOne.
Current JDE E1 Patches
Many of the patches that Oracle release fix security issues that could be exploited over the network without any authentication. These could be used to trigger a system crash, or allow data to be accessed. Due to the nature of E1, the vulnerabilities that the patches address are mainly exposed on internal networks that are open to exploitation by malicious software or a disgruntled employee. However, the increasing use of E1 with internet facing technologies like E1 Mobile, Business Services, Orchestrator, or REST Web Services, now make it increasingly likely that software vulnerabilities may potentially be exposed to the internet. Not applying security patches to internet facing systems significantly increases the risk of them being exploited.
So it is definitely worth taking a look to see what patches for JDE E1 might be relevant to you – Oracle release quarterly Critical Patch Updates (CPU) and the latest information is available here.
July 2019’s notice included four new advisories for E1, CVE-2017-5645, CVE-2018-19362, CVE-2018-1559 which effect the HTML Server component. This is described in Knowledge Doc ID 2494858.1. The National Vulnerability Database (NVD) assigns two these vulnerabilities with a severity of 9.8 (Critical).
“CVE-2017-5645 Vulnerability in the JD Edwards EnterpriseOne Tools component of Oracle JD Edwards Products (subcomponent: Installation SEC (Apache Log4j)). The supported version that is affected is 9.2. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise JD Edwards EnterpriseOne Tools. Successful attacks of this vulnerability can result in takeover of JD Edwards EnterpriseOne Tools.”
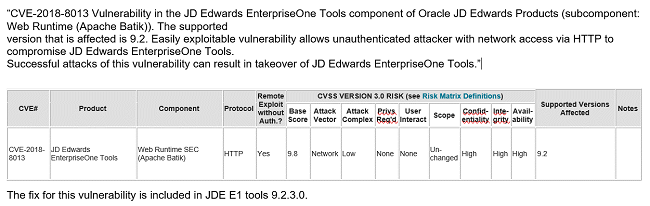
The fix for this vulnerability is included in JDE E1 tools 9.2.3.4.
If you haven’t upgraded the E1 tools release recently, you might also review the previous advisories. The October advisory included three vulnerabilities for E1, CVE-2018-7489, CVE-2018-15095, CVE-2018-0739.
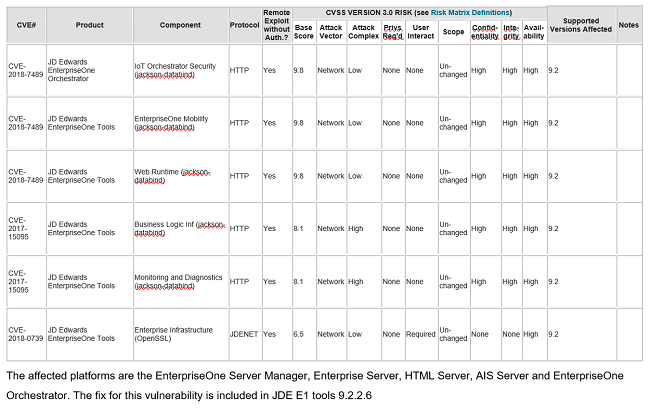
The affected platforms are the EnterpriseOne Server Manager, Enterprise Server, HTML Server, AIS Server and EnterpriseOne Orchestrator. The fix for this vulnerability is included in JDE E1 tools 9.2.2.6
Don’t forget the underlying technologies
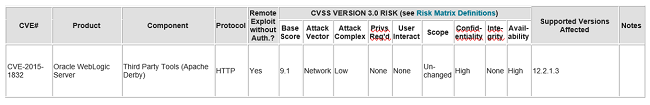
The technologies that support E1 may be even more susceptible to these risks. Oracle WebLogic Server is a key component of the E1 architecture and is often overlooked for patching. Doc ID 551453.1 describes, ‘How to Find the Correct Critical Patch Update Patches for Oracle Fusion Middleware Products’.
April’s CPU for WebLogic Server contained fourteen vulnerabilities with a Common Vulnerability Scoring System (CVSS) of 9.8. Several of these issues effect the core WLS components and these are important for EnterpriseOne. CVSS is an industry standard system for scoring security flaws from 1 to 10 where 10 is the most severe. To put this into a bit of perspective, the Spectre and Meltdown bugs that the press have been making a fuss about have a CVSS of 5.6 (See NIST).
Most sites that use Oracle database will already have a patching policy in place for these systems, and in a recent survey 50% of respondents apply the CPU within six months. However, 15% of respondents admitted that they never apply the updates!
Interestingly, there are less CPU for Oracle database than there are for Oracle WebLogic Server.
Many other Oracle products that are part of the Fusion Middleware family and are frequently used with E1 are also included on the Critical Patch Updates. These include Oracle HTTP Server, Oracle JDeveloper, Oracle BIEE, Oracle Access Manager and last but by no means least JAVA – which pervades almost everything!
If you are wondering what the latest patches are, and how to get them, have a look at Doc ID 2568292.1. This is the Patch Availability Document (PAD) and lists patches for Oracle Database, Fusion Middleware, and Enterprise Manager for October 2019.
Has the version of JAVA on the WebLogic server been updated recently?
The significance of Oracle Fusion Middleware, especially WebLogic Server, is that this is most likely the software in the front line of any E1 installation.
Critical Fixes
As well as quarterly CPUs, Oracle release Security Alerts ‘for vulnerability fixes deemed too critical to wait for distribution in the next Critical Patch Update’. These updates will address urgent issues in a specific product. An example of this is CVE-2018-3110 which was released in August 2018. This fixes a high-risk issue in Oracle Database (11.2.0.4 and 12.2.0.1) that has a CVSS score of 9.9 and “could result in takeover of Java VM”.
Start 2020 with a plan
So, if you have now decided that you really do need to deploy some of the updates, it is time to make a plan.
To assist with planning and the scheduling of downtime, the release dates for Critical Patch Updates are announced a year in advance:
- January 14, 2020
- April 14, 2020
- July 14, 2020
- October 20, 2020
With these timings, you can then assess if you are likely to have the resource/expertise available. Even if you don’t currently outsource for maintenance, this sort of expertize can still be outsourced on a project basis.
So, looking ahead to 2020, here are my suggestions for some New Year patching resolutions
- If you are not already receiving the email notifications for the Critical Patch Updates then sign up here. You should also review Oracles Security Fixing Policy which is detailed here.
- In our experience it is very unusual for a patch to cause an issue with E1 however it happens. If unscheduled downtime is unacceptable then have an E1 test system to load and test the patches before applying to the production system. This does not need to be elaborate. The test system might just comprise of an Enterprise and WebLogic server.
- Have a documented policy that assesses the risks of software vulnerabilities and put a procedure in place to address these critical updates. If you outsource the maintenance or hosting of JDE then check your suppliers patching policy
Explore DWS’ full range of testing products and DevTech services, including Dimension LoadTest™, Dimension SwifTest™ and Dimension Focus™.




